Setup Prerequisites
Before installing Ego, ensure that the following tools and services are installed and properly configured. While you can choose any platform, we recommend Linux for optimal performance and compatibility.
Docker
- For ease of use, we recommend using Docker Desktop
- If you prefer using the command line, you can install the Docker Engine here
PostgreSQL
- We store all Ego related data within PostgreSQL databases
- Instructions for downloading and installing PostgreSQL can be found here
- We also provide a docker quickstart for database setup below. This does not require PostgreSQL installation
Setup Identity Provider Secrets
- You will need a
Client IDandClient Secretfor at minimum one OAuth 2.0 identity provider (more information below)
- You will need a
PostgreSQL Quickstart
We will be using docker to set up our PostgreSQL database for Ego.
- Pull and Run PostgreSQL
Use the following command to pull and run the PostgreSQL docker container:
docker run --name postgresEgo -e POSTGRES_PASSWORD=abc123 -e POSTGRES_DB=egoDb -p 5432:5432 -d postgres
This command spins up a PostgreSQL container named postgresEgo with the default username postgres, password of abc123 and creates a database within it called egoDb.
- Pull and Run PgAdmin4 (optional)
PgAdmin4 is an open-source, web-based tool that provides a convenient and user-friendly interface for managing PostgreSQL databases. Use the following command to pull and run the PgAdmin4 docker container:
docker run --name my-pgadmin -p 82:80 -e 'PGADMIN_DEFAULT_EMAIL=email@domain.com' -e 'PGADMIN_DEFAULT_PASSWORD=abc123' -d dpage/pgadmin4
This command spins up a PgAdmin4 container accessible from http://localhost:82/. Once deployed you will need to login using the credentials specified within the docker run command. In our example above this is email@domain.com with the password abc123.
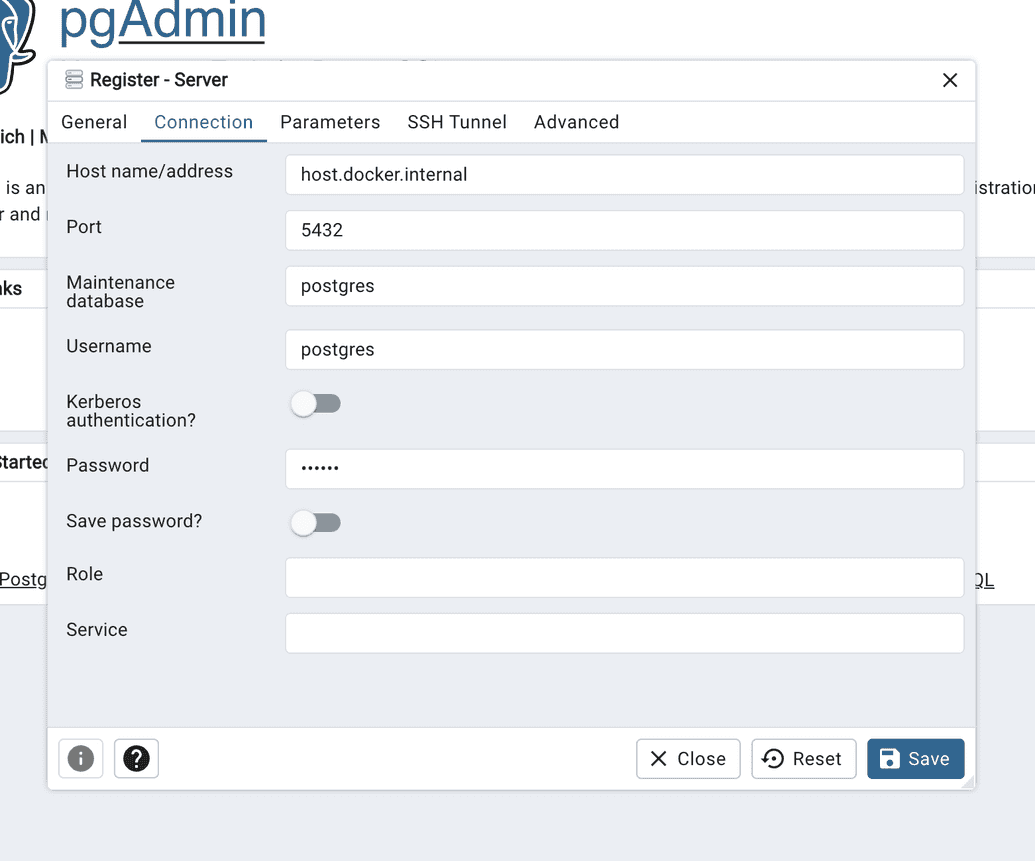
- Connect your database to PgAdmin4 (optional)
Select Add New Server name your server and then select the connection tab and input the following:
These values may be different depending on the values you provided during step 1
| Field | Value |
|---|---|
| Host name/address: | host.docker.internal |
| Port: | 5432 |
| Username: | postgres |
| Password: | abc123 |
- Click Save
From the left-hand server drop-down, you can now view the connected database(s)
Setting up Identity Provider Secrets
To properly use the identity providers with Ego, OAuth credentials must be set up with each provider you want to use, specifically a client ID and client secret.
The secret is known only to your web application and the provider's authorization server. It serves to protect your resources by only granting tokens to authorized requestors.
 Secrets Managment Software
Secrets Managment Software
If you or your organization needs a secure solution to store, manage, and control access to all your secrets in one place, you may wish to consult with your IT department about adopting a 3rd party tool such as HashiCorp's Vault.
Each identity provider has a different process for setting up their client secrets. Linked below are summaries for setting up each available identity provider: